Integrate Azure AD as a OIDC for SSO with Portworx Backup
This topic explains how you can integrate Azure Active Directory (AD) as a OIDC for SSO with Portworx Backup HTTPS access enabled endpoint.
Prerequisites
- Ensure you have an EKS cluster, Route 53 with a Register domain for which you can use an SSL certificate from AWS Certificate Manager (ACM) using Azure AD for SSO login.
- Attach the additional role
ALBIngressControllerIAMPolicy, and ensure to attach this role to your EKS cluster. Without attaching this role, you cannot launch the Application Load Balancer (ALB).
Integrate Azure AD with Portworx Backup
To integrate Azure AD with Portworx Backup:
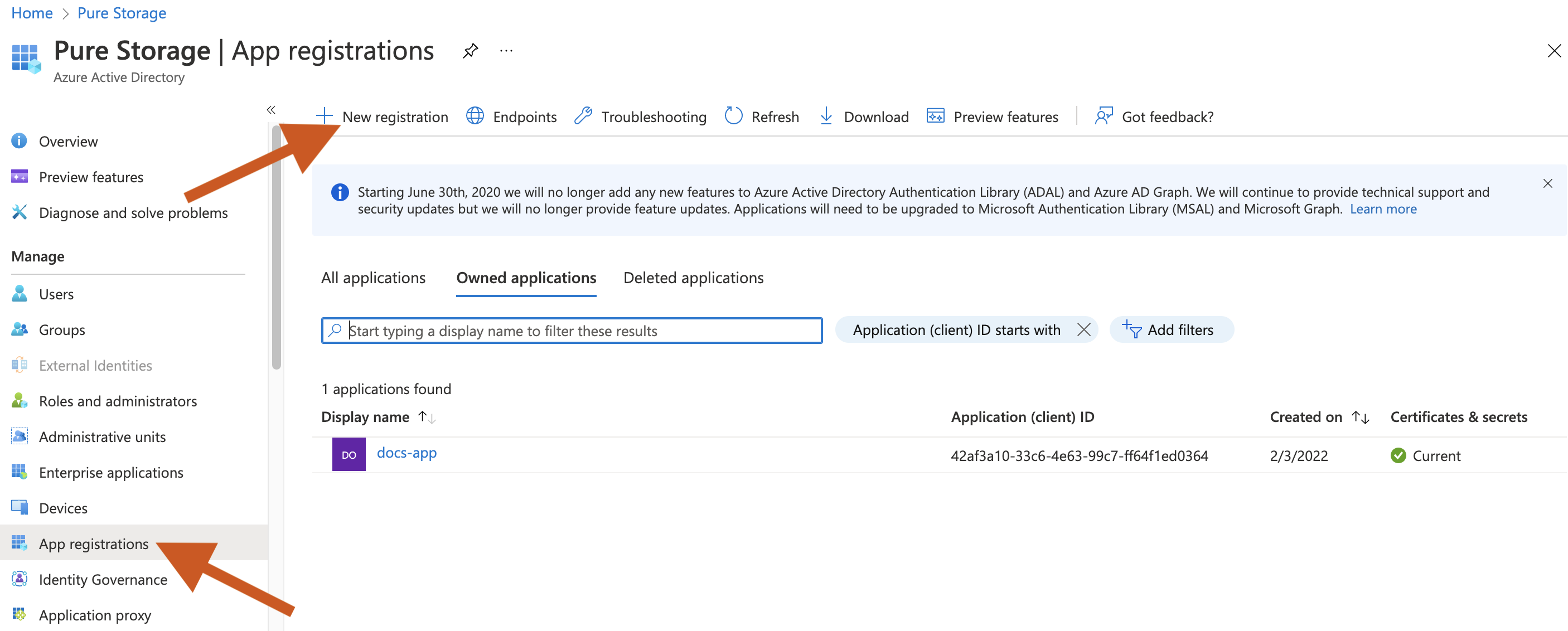
Login to the Azure portal, and select View from the Manage Azure Active Directory.
In the Azure AD page, select App registrations from the left pane -> New registration.
In the Register an Application page, fill-in the Name text box, choose an option from the Supported account types, and click Register.
Your application is created.
In the Azure AD page, select App registrations -> Owned applications tab.
Select your application. The Overview page displays all details about your application. Make a note of the Application (client) ID, which you can use while generating the Portworx Backup spec.
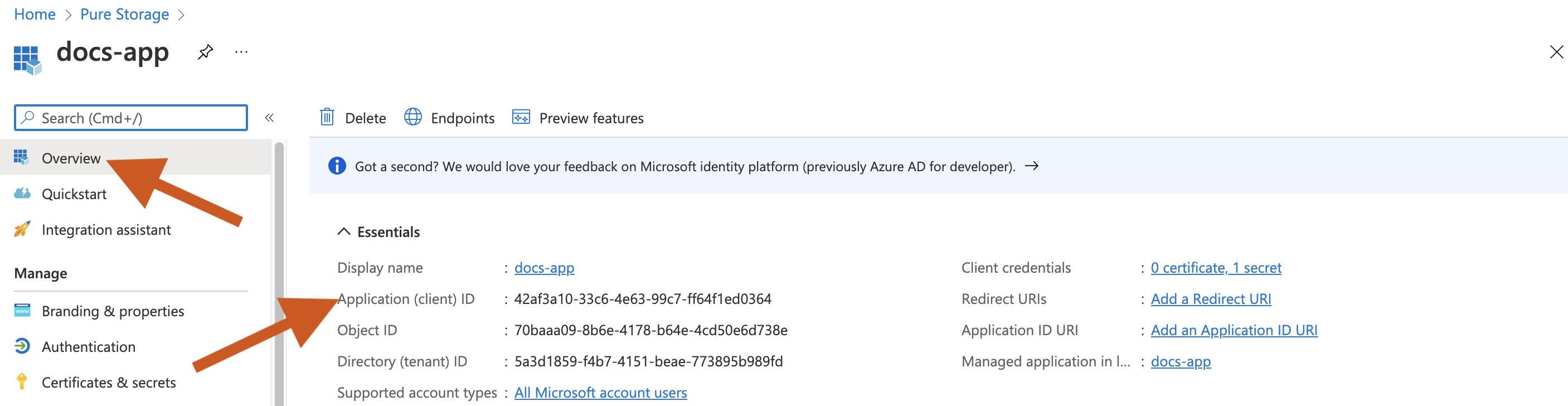
Select Certificates & secrets in the left pane -> New client secret to add a client secret for the application.
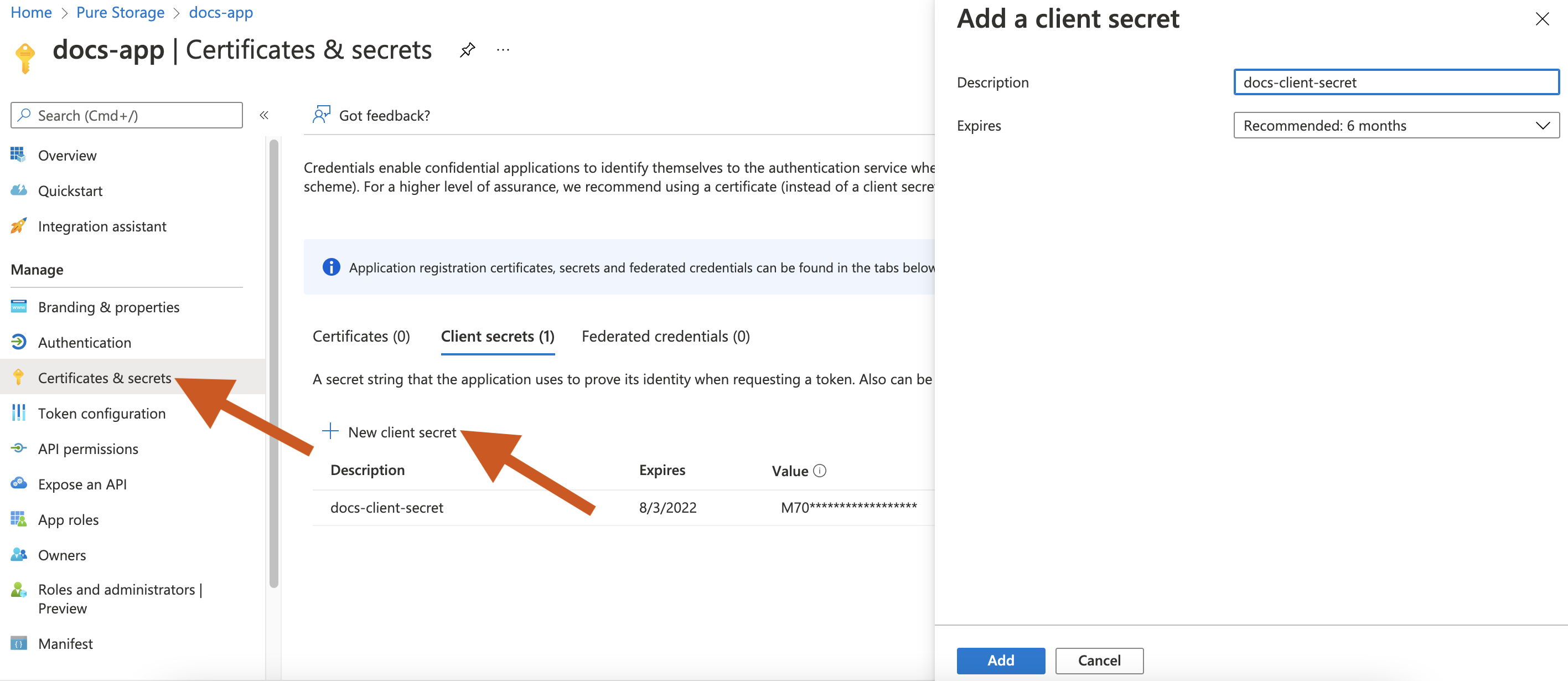
In the Add a client secret window that appears, enter the client secret description and choose the validity of client secret from the Expires dropdown list.
Click Enter to add a secret for your application. You can use this secret while generating the Portworx Backup spec.
Get the OIDC endpoint by selecting the application you created -> Endpoints tab. Copy only the first two parts from the Endpoints window.
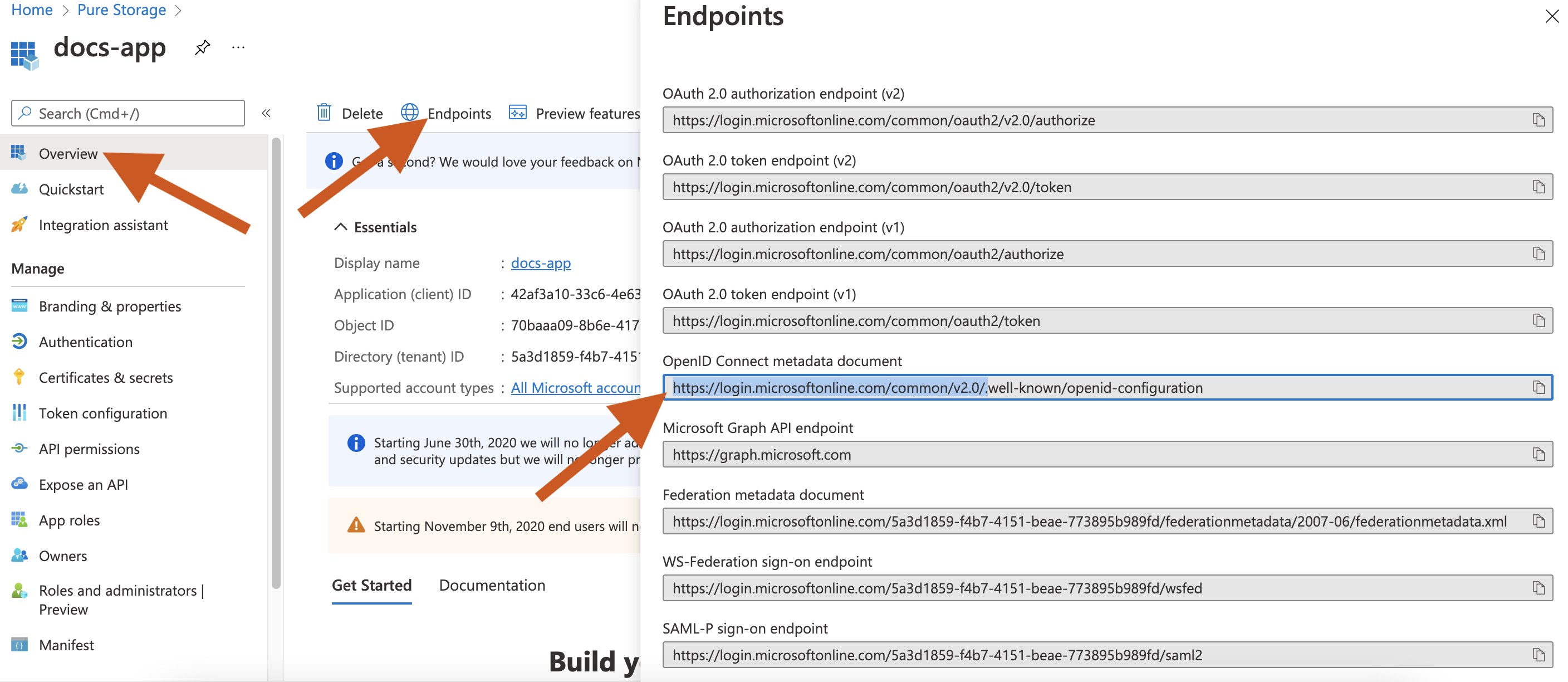
Using the Portworx Central spec gen wizard, generate Portworx Backup spec and use the client ID, secret, or endpoint.
Install the generated spec.
Add an external OIDC provider as the identity provider in Portworx Backup
After integrating the Azure AD or an external OIDC with Portworx Backup, perform the following steps to add any external OIDC provider in Portworx Backup:
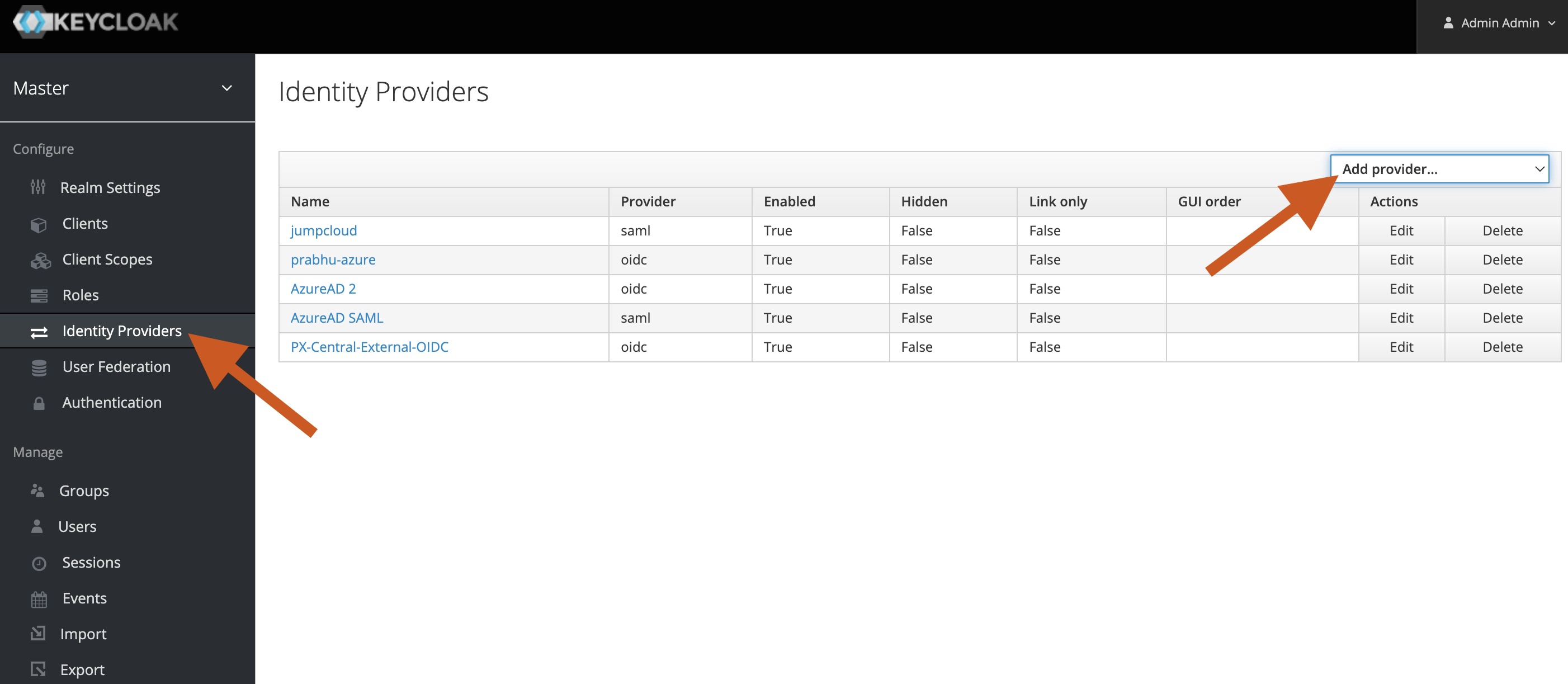
Log in to Keycloak using administrator credentials, and select Identity Provider from the left pane.
In the Identity Providers page, select OpenID Connect v1.0 from the Add provider… dropdown list.
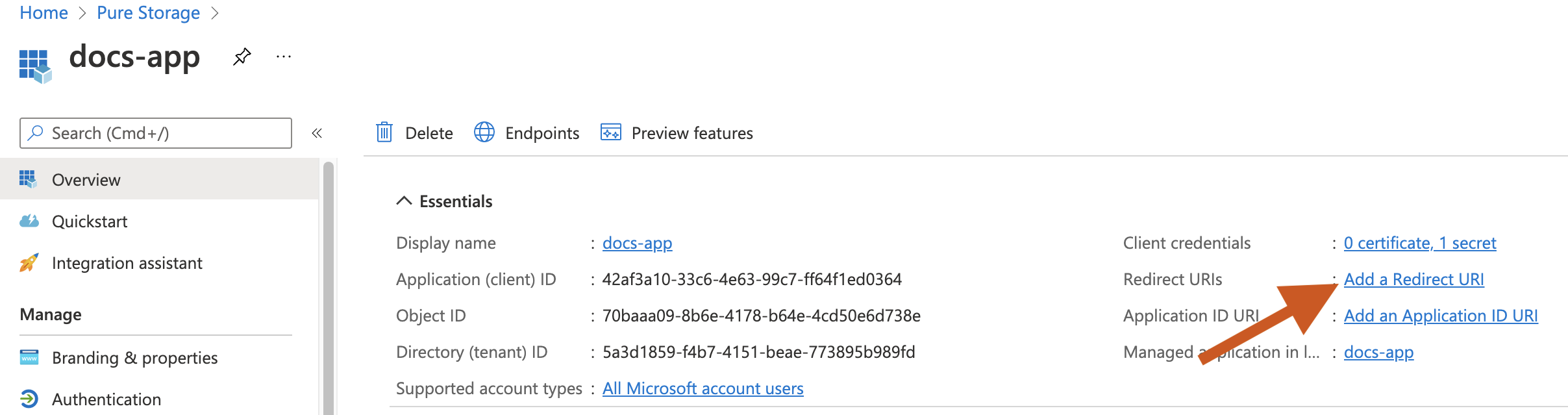
From the Add identity provider page, copy the URI from the Redirect URI text box, and paste it in your OIDC provider. For example, in Azure AD, navigate to your application Overview page, click Add a Redirect URI in the Redirect URIs section, and paste the URI in the Authentication page, and click Save.
Navigate to the Keycloak -> Add identity provider page -> OpenID Connect Config section, and enter the following fields:
- Authorization URL and Token URL: Paste the URLs that you copied from the Azure AD -> your application Authentication page.
- Logout URL: Paste the URL that you copied from the Azure AD -> your application Overview page -> Endpoints page.
- Client Authentication: From the dropdown list, select Client secret sent as post.
- Client ID: Paste the Application (client ID) that you copied from the Azure AD -> your application Overview page -> Essentials section.
- Client Secret: Paste the secret value that you copied from the Azure AD -> your application Certificates & secrets page.
Click Save.
Using a browser, access Portworx Backup without
/auth. Your OIDC provider link appears on the login page:
You can click the link to login with your Keycloak user credentials.
Note: All new users that login from external Keycloak are, by default, assigned to the application user role.
